Remember the HT Coin Android malware issue that we reported about a couple of weeks ago? The HelloTalk app displayed notifications, which when tapped, downloaded a malicious APK and installed in on the user's phone.
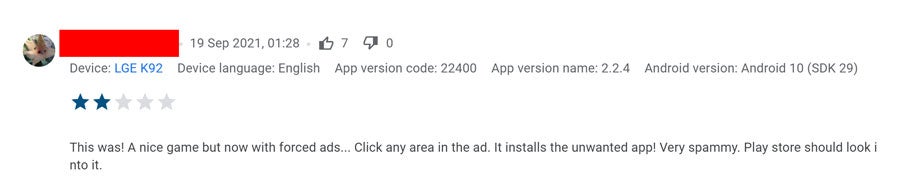
A few days ago, a game developer (Rifter Games) shared their troubles on reddit's r/androiddev. According to them, some of their users recently started leaving negative reviews for their game. Other users had upvoted the reviews, which in turn grabbed the developer's attention. The users alleged that the game displayed some ads, which when interacted with, resulted in a third-party app being downloaded, and installed without the user's consent.
What was alarming here is the manner in which the app in question was downloaded. You see, the ad didn't open the Google Play Store, or prompt the user to click the install button. Instead, the malware was downloaded directly when the user touched the ad, i.e., it bypassed Google Play completely. That is eerily similar to the other problem that we saw, isn't it?
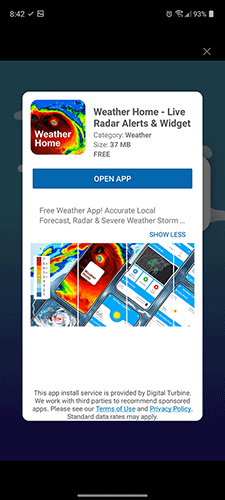
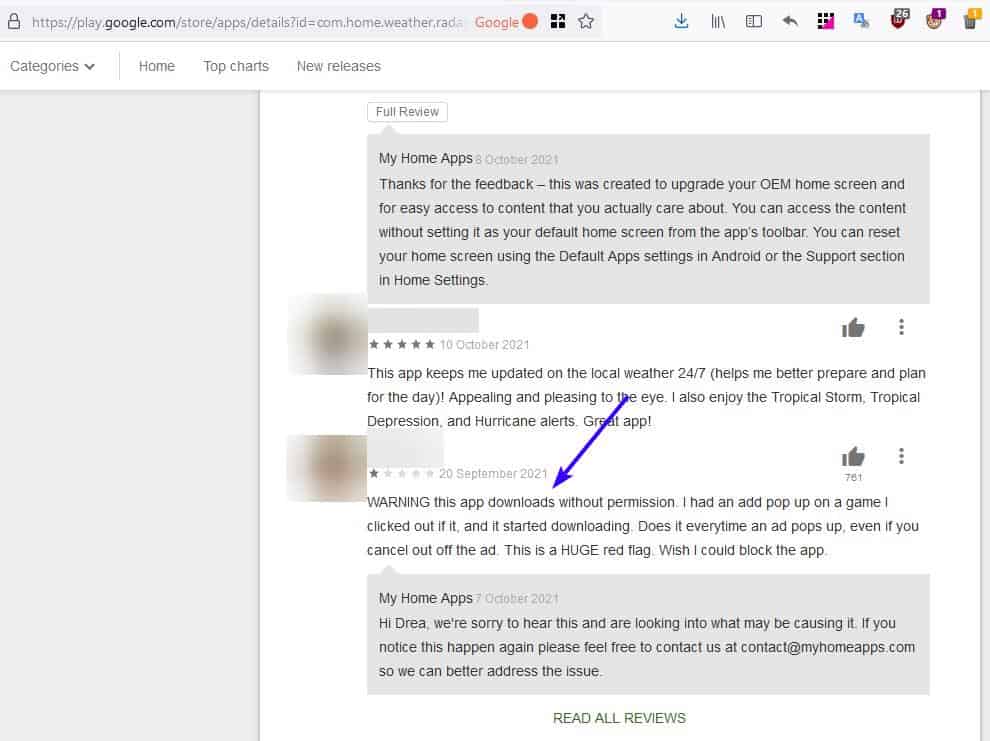
The game developer contacted the users, and as them to provide additional information, and managed to get some screenshots related to the issue. The images show what appears to be an interstitial ad, aka a full-screen ad, that promotes an app called Weather Home -Live Radar Alerts & Widget. It has an X button at the top, but did those users tap it to close the ad? The second image clearly indicates that the app is being downloaded.
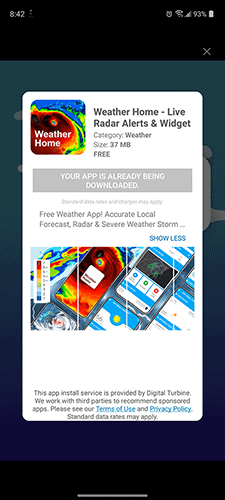
The game developer says they reached out to their ad providers, seeking an answer to their issue. They were informed that the technology behind the app install, i.e. the one that bypasses the Google Play Store, belongs to a company called Digital Turbine. If you observe the screenshots of the ads closely, you'll notice the wording at the bottom reads, "This app install service is provided by Digital Turbine." What is DT? It is a digital advertising company that provides DSP (demand-side platform), and recently acquired an app monetization company called Fyber.
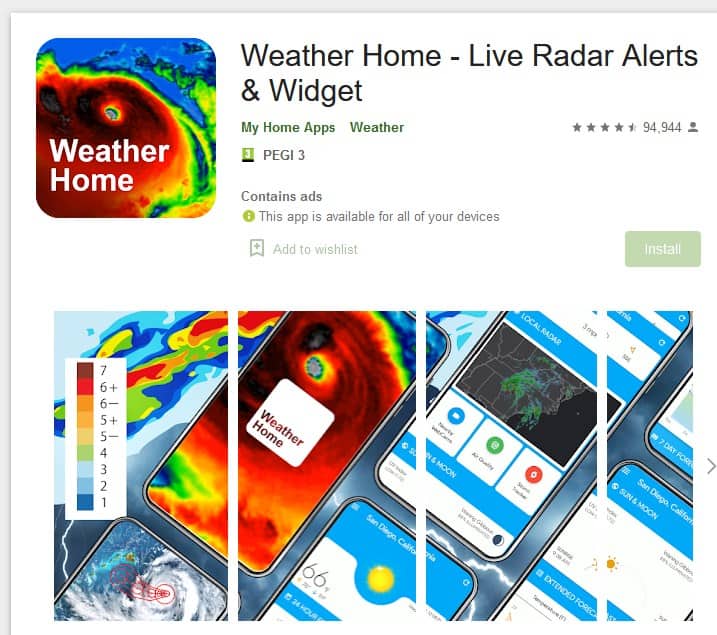
Shouldn't Google Play Protect prevent this app install, or at least flag the app in question? This is where it gets interesting. The weather app that was downloaded, is available on the Google Play Store, which is probably why it didn't get flagged. Some of the app's recent reviews say that the user did not choose to install the app, and that it was installed automatically. Whether the app is safe or malicious remains a mystery, but the bigger issue is the way it got installed.
Believe it or not, this company has patented the technology to serve app downloads by bypassing Google Play. (Reference: 1, 2)
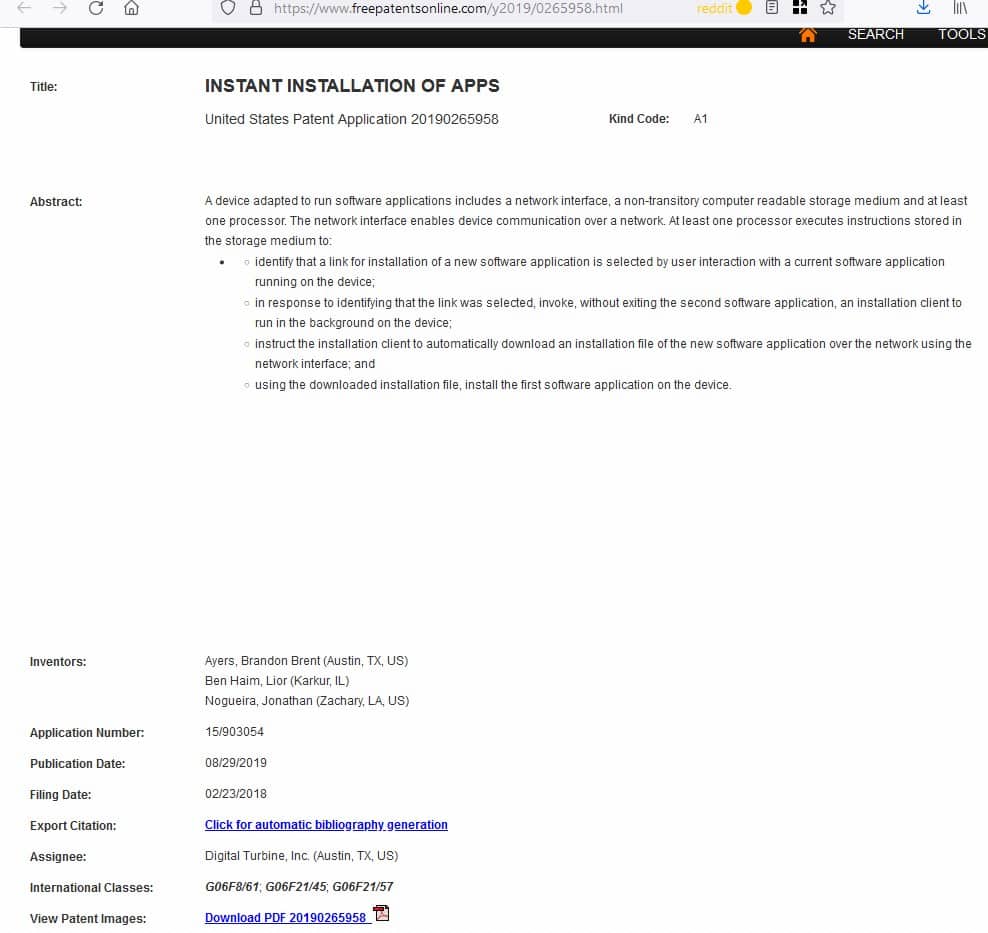
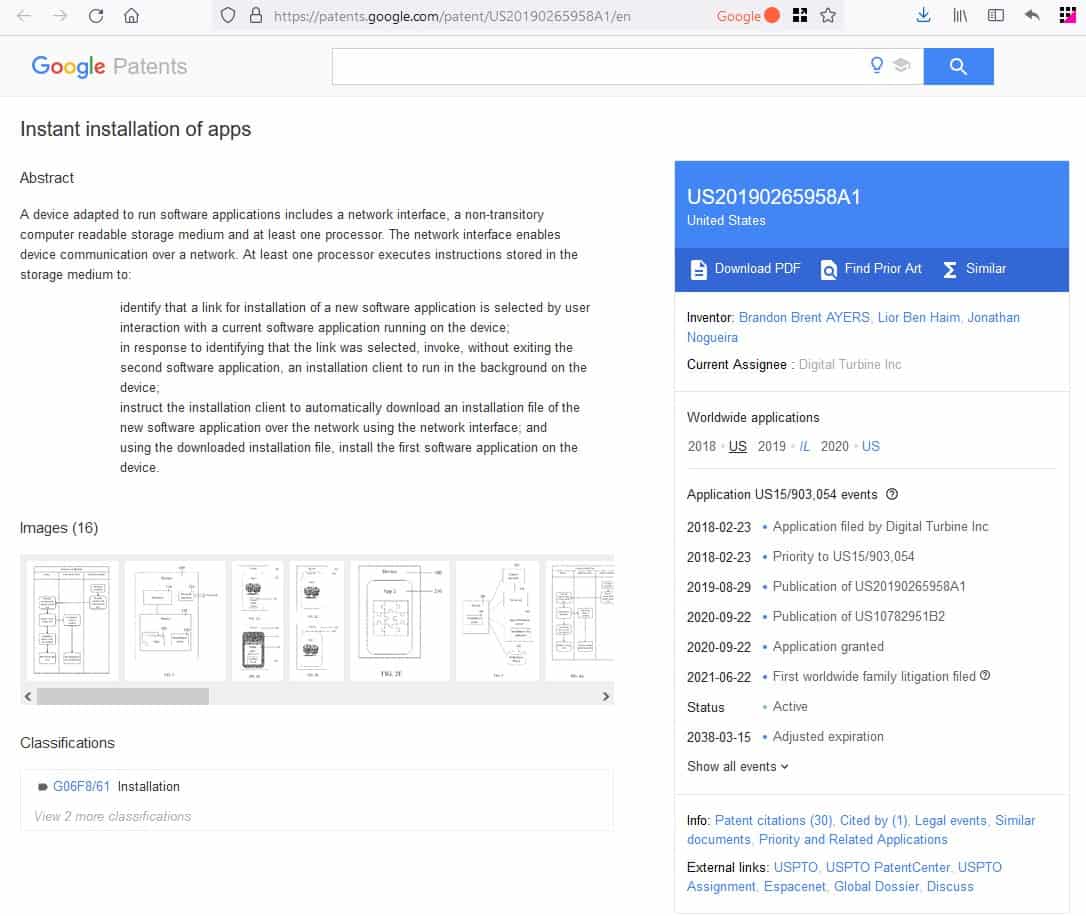
Here's an extract from the patent's page.
Embodiments described herein utilize an installation client on a device in order to install apps on a device without redirecting the device to an app store. The content provided to the device includes links (denoted here “instant install links”) which indicate that the associated app should be installed by the installation client and not via an app store. When an instant install link is selected, the installation client is invoked to run in the background. The installation client downloads the installation file for the app associated with the instant install link to the device. The new app may then be installed on the device using the installation file.
A comment on that reddit thread by u/omniuni explains more about this. Many phones, especially carrier-locked variants, ship with an app called DT Ignite (reference: Android Central). This is a system level app, that carriers can use to push bloatware apps to your device. That's how the ad managed to install the app on the users' phones, because DT's app allows it.
The user says Digital Turbine replied in context to the post. The company is apparently looking into the issue to figure out how the app download started when users tapped the X button. So, it appears that users did tap the X button after all, but the ad initiated the app download anyway. The user says that Digital Turbine's representative assured them that all app packages were verified before and after they are installed, and are registered with Google Play. The download is delivered via a secure connection.
A security issue related to this has been filed on Google's Issue Tracker portal. This case may not have been malicious, but it is definitely creepy and poses a serious privacy and security issue for users. What if a malware somehow slips through this method?
Malware and mobile ads aren't a new combination. If you use a mobile browser without an ad-blocker, you may come across different kinds of ads. Some of these may claim your phone is infected with a virus, and gives you an option to install a free antivirus. These are nothing but scareware tactics to fool the user into that their device is at risk, and when they tap on the ad, it turns out to be the malware.
You can protect yourself from trackers and ads by using a system-wide ad blocker like Adaway (has a non-root option) or Blockada or DNS66, or a DNS solution like (AdGuard, NextDNS). If that's not a viable option, I recommend using a browser like Firefox with uBlock Origin to help prevent ads, though it won't disable ads in other apps.
What do you think about silent app installs via ads?
Thank you for being a Ghacks reader. The post Android game developer says some ads were able to bypass Google Play to install third-party apps appeared first on gHacks Technology News.
https://ift.tt/3avDGsQ
from gHacks Technology News https://ift.tt/3v4jRSH


No comments:
Post a Comment