Microsoft will remove support for root certificates with kernel mode signing capabilities in the Microsoft Trusted Root Program in the first half of 2021.
The change affects devices running Microsoft's Windows 10 operating system only, and drivers that have expired as part of the change won't load, run or install anymore on Windows 10 devices.
| Driver runs on | Drivers signed before July 1 2021 by | Driver signed on or after July 1 2021 by |
|---|---|---|
| Windows Server 2008 and later, Windows 7, Windows 8 | WHQL or cross-signed drivers | WHQL or drivers cross-signed before July 1 2021 |
| Windows 10 | WHQL or attested | WHQL or attested |
Microsoft published a list of expiration dates for trusted cross-certificates; all listed trusted cross-certificates will expire either in February 2021 or April 2021.
Commercial release certificates, publisher certificates and commercial test certificates will become invalid on the expiration date, and that means that drivers signed with these certificates will become unusable as well.
[..] all software publisher certificates, commercial release certificates, and commercial test certificates that chain back to these root certificates also become invalid on the same schedule.
Microsoft informed hardware developers about the changes to its Trusted Root Program in early 2019. The majority of drivers should continue to work as before, but it is possible that older drivers, e.g. drivers that have not been updated for years, may stop working as a consequence.
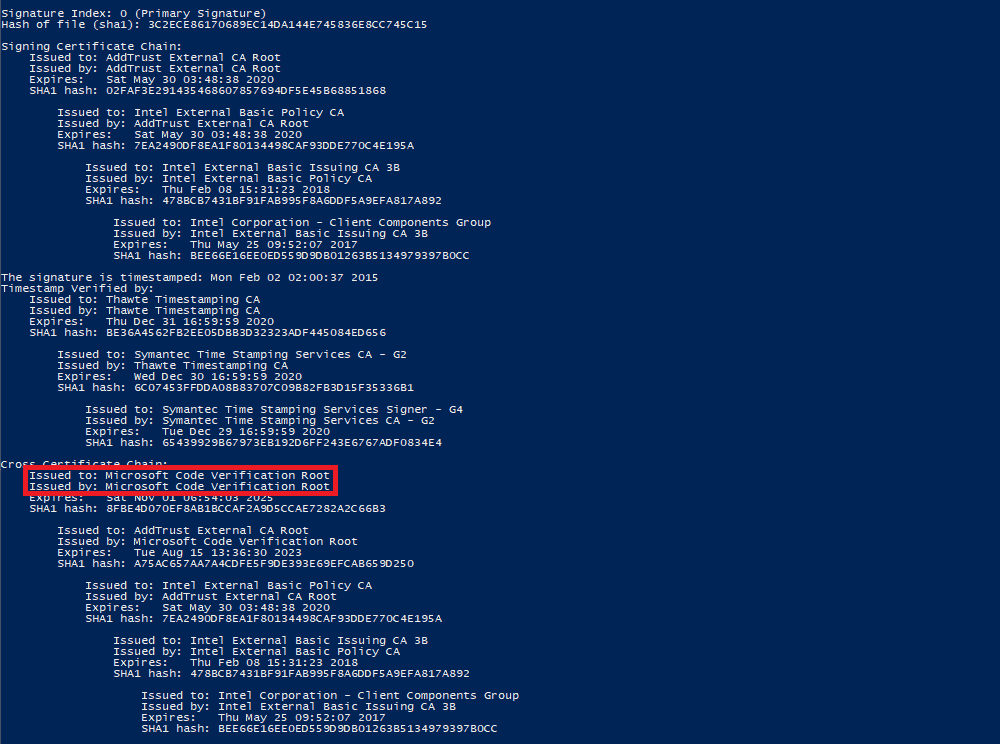
The command line tool SignTool.exe, installed automatically with Visual Studio, can be used to verify if a driver will continue to work. All it takes is to run the command signtool verify /v /kp <mydriver.sys> (replace <mydriver.sys> with the driver name) and check if the Cross Certificate Chain ends in Microsoft Code Verification Root. If that is the case, the signing certificate is affected.
Windows customers who are affected by the change, e.g. when they run older hardware with drivers that have not been updated by the manufacturer in a while, have only a few options to deal with this. If a driver update is not available, disabling driver signature enforcement is an option; this reduces system security and may also impact stability. It is recommended to create a backup before making the change.
One of the easier options to disable driver signature enforcement is to run the following command from an elevated command prompt: bcdedit.exe /set nointegritychecks on.
To restore the old status quo (default), run bcdedit.exe /set nointegritychecks off instead from an elevated command prompt. (via Deskmodder)
Thank you for being a Ghacks reader. The post Reminder: supports for root certificates with kernel mode signing capabilities ends next year appeared first on gHacks Technology News.
https://ift.tt/2KKwoaU
from gHacks Technology News https://ift.tt/33tO9li


No comments:
Post a Comment